Security and Threat Protection
How to enable or disable threat protection and request schema validation.
This is a legacy documentation page for the previous interface.For the latest page, see Hub Listing - Gateway Tab
Security FunctionalityFor Enterprise Hub customers, all of the security functionality described below is available only if the API uses Rapid Runtime to proxy/protect the backend API.
The Security tab has multiple configurations that you can use to protect your API.
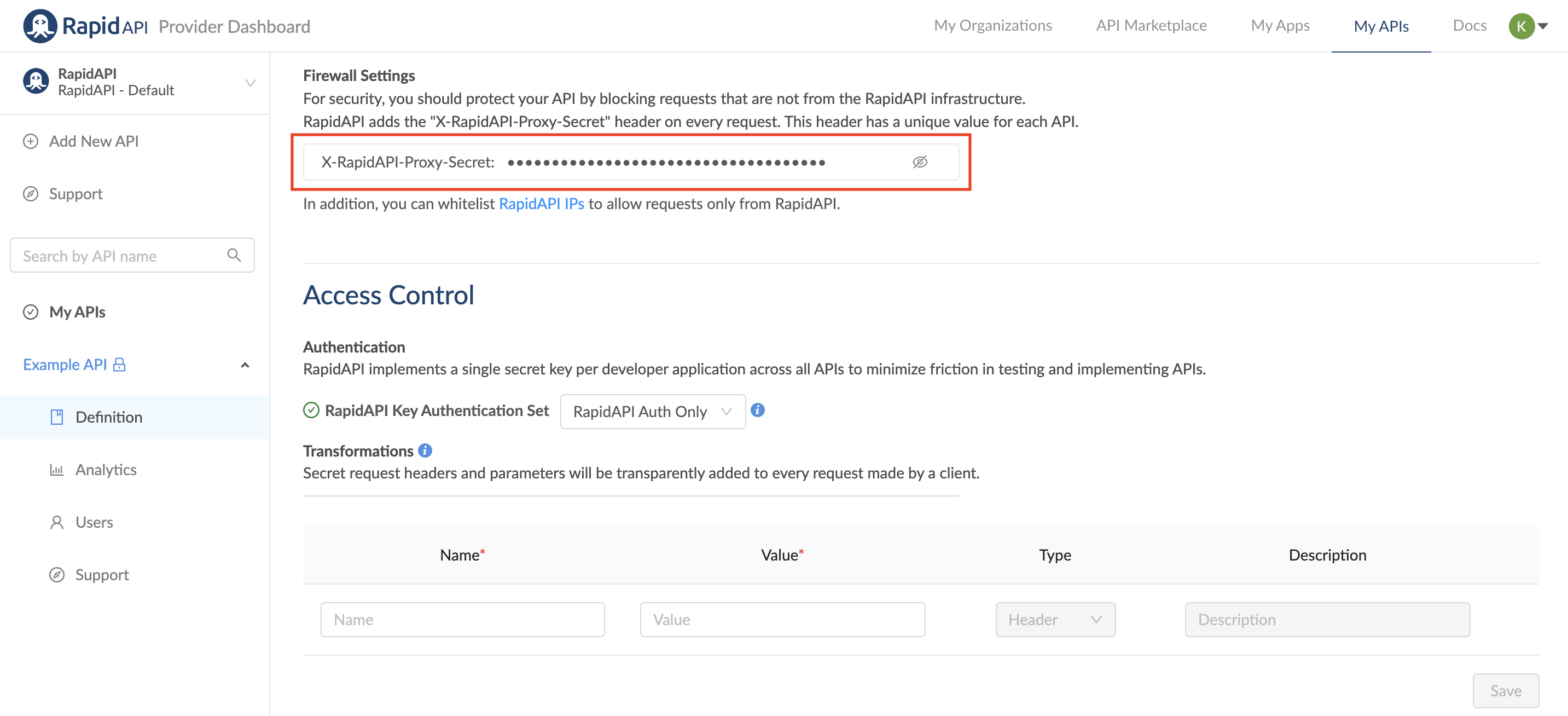
Firewall settings
For security reasons, you should protect your API and block requests coming from outside the Rapid infrastructure.
Rapid adds the X-RapidAPI-Proxy-Secret header on every request. This header has a unique value for every API, and if the header is missing or has a different value, you can assume the request is not coming from our infrastructure. The header for this API is: X-RapidAPI-Proxy-Secret followed by a unique string.
List of IP addresses used by Rapid
Every request coming from the Rapid network will come from the following IP addresses. You can allow list these IPs, as they are the ones used to send requests only from Rapid.
A request coming from Rapid can be considered already authenticated, so no billing or authentication checks are required on the API side.
Here is the complete list of IPs to allow list:
Notice that you must accept API requests from ALL IPs below, regardless of which region your servers are located in.
Region | IPs |
|---|---|
US East | 3.235.211.187 |
US West | 35.162.152.183 |
Mumbai | 13.127.146.34 |
Tokyo | 13.112.233.15 |
Frankfurt | 3.64.99.234 |
Sydney | 13.54.58.4 |
South America | 18.228.69.72 |
Singapore | 3.0.35.31 |
Ireland | 34.250.225.89 |
Canada | 3.96.250.82 |
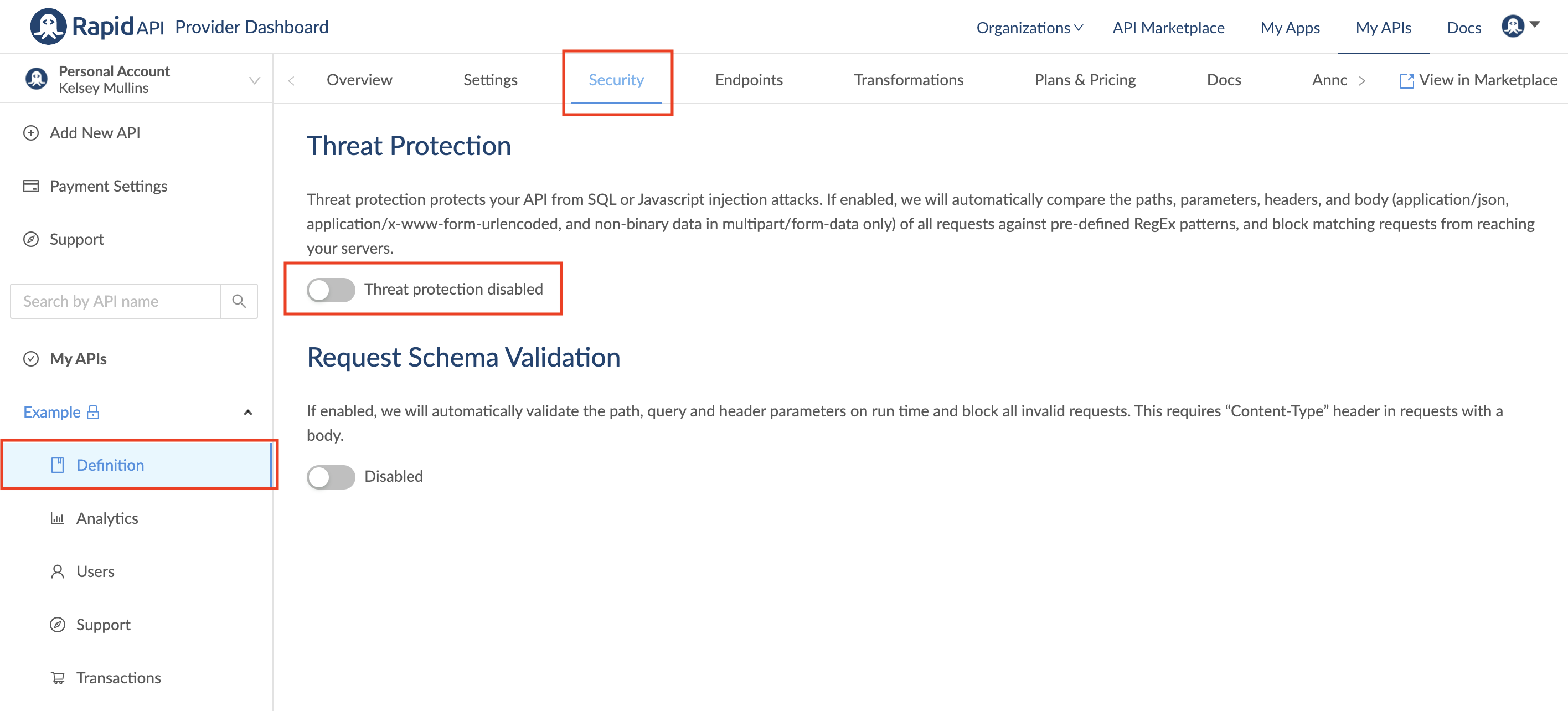
Threat protection
You can enable or disable threat protection under the Security tab of your API's definition. Threat protection protects your API from SQL or JavaScript injection attacks. If enabled, we will automatically compare the paths, parameters, headers, and body (application/json, application/x-www-form-urlencoded, and non-binary data in multipart/form-data) of all requests against pre-defined RegEx patterns, and block matching requests from reaching your servers.
By default, threat protection is off. You can toggle it on or off by clicking the switch.
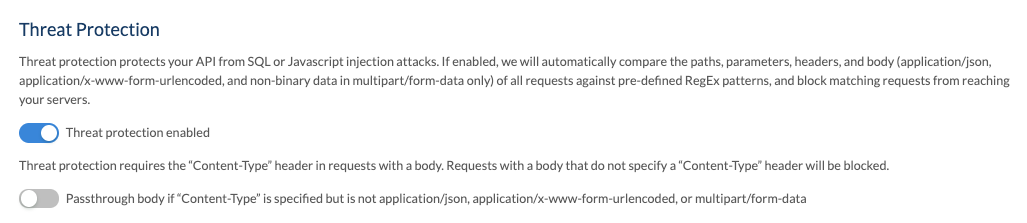
If threat protection is enabled, the Content-Type header must be specified if the request has a body. If Content-Type is not specified, the request will be blocked. You can configure whether to block or pass the body through if the Content-Type is not set to application/json, application/x-www-form-urlencoded, and non-binary data in multipart/form-data.
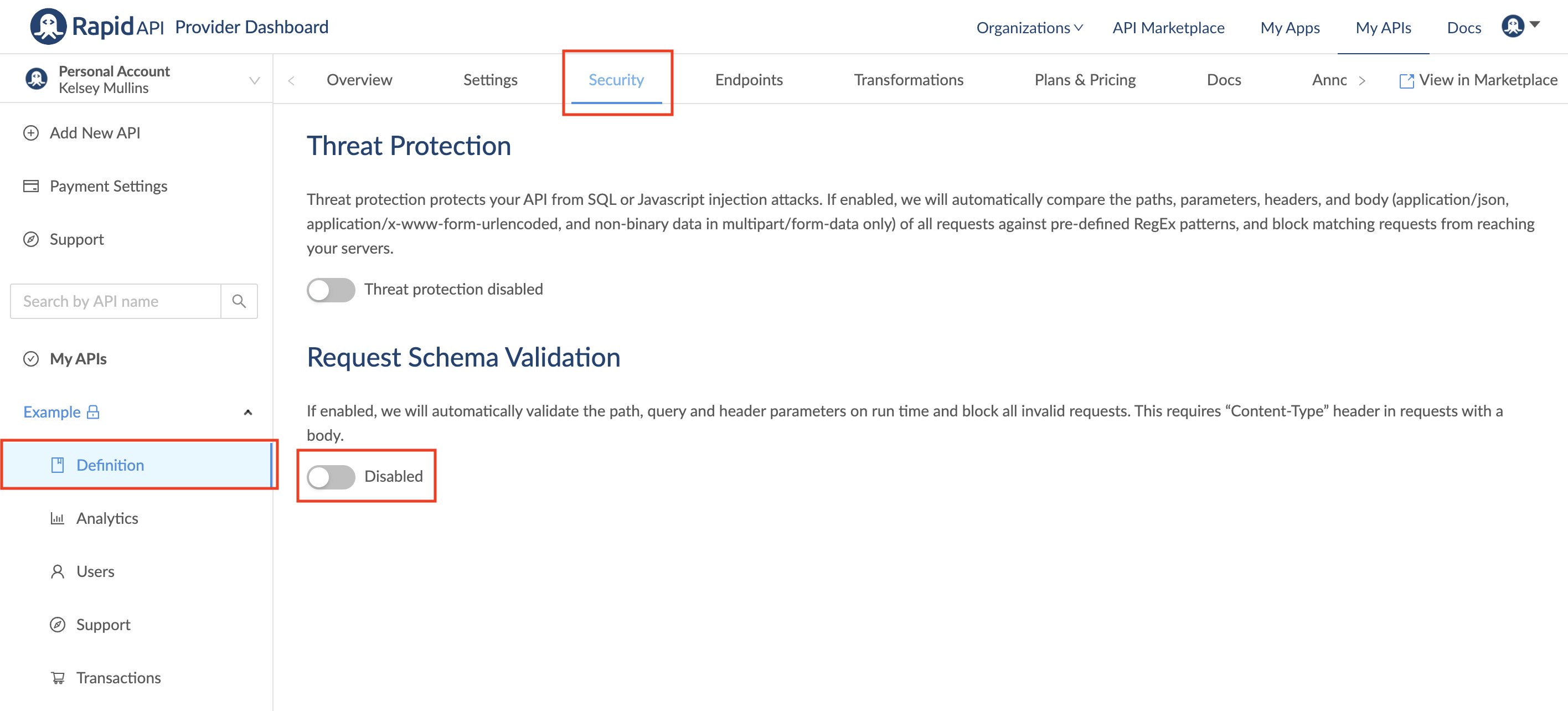
Request schema validation
You can enable or disable request schema validation under the Security tab of your API's definition. This stops requests that have a validation error at our Rapid Runtime so the call will not be sent to your API hosting server.
If enabled, we will automatically validate the path, query, and header parameters on run time and block all invalid requests. This requires a "Content-Type" header in requests with a body. By default, request schema validation is off. You can toggle it on or off by clicking the switch.
Additional request schema validation settings
When Request Schema Validation is enabled, you will be able to choose from three settings:
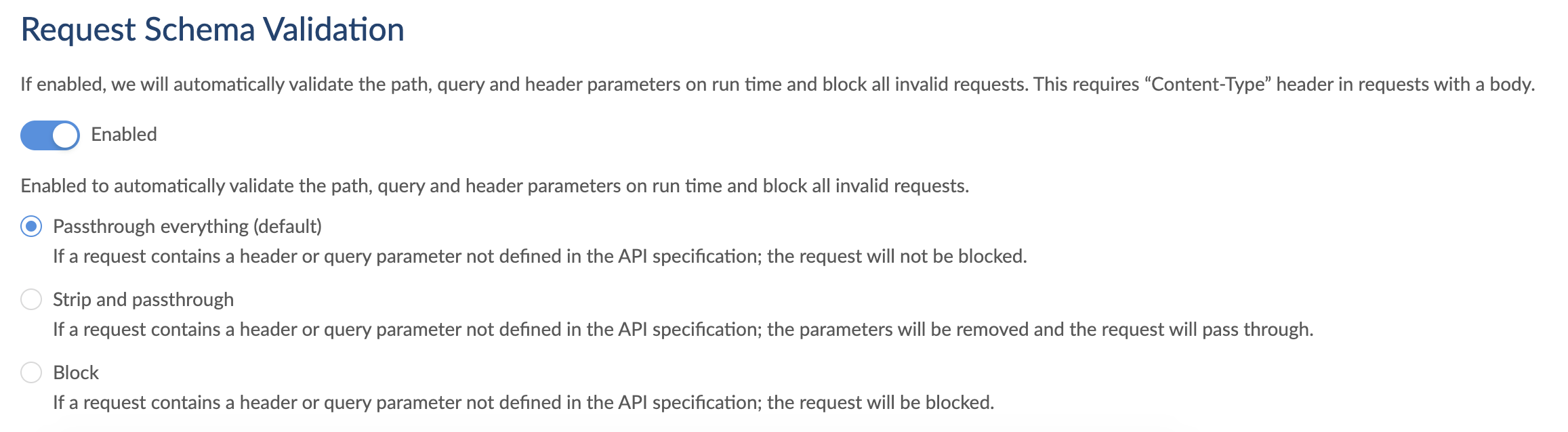
Pass through everything (default): Request passed through without stripping any parameters or headers.
Strip and passthrough: Strips unexpected parameters or headers and passes the request through.
Block: Blocks any request with unexpected parameters or headers.
Currently, even if the default HTTP headers or auto-generated headers for REST APIs are not explicitly defined in the specification the request will be blocked if you select "Strip and passthrough" or "Block"
Request size limit
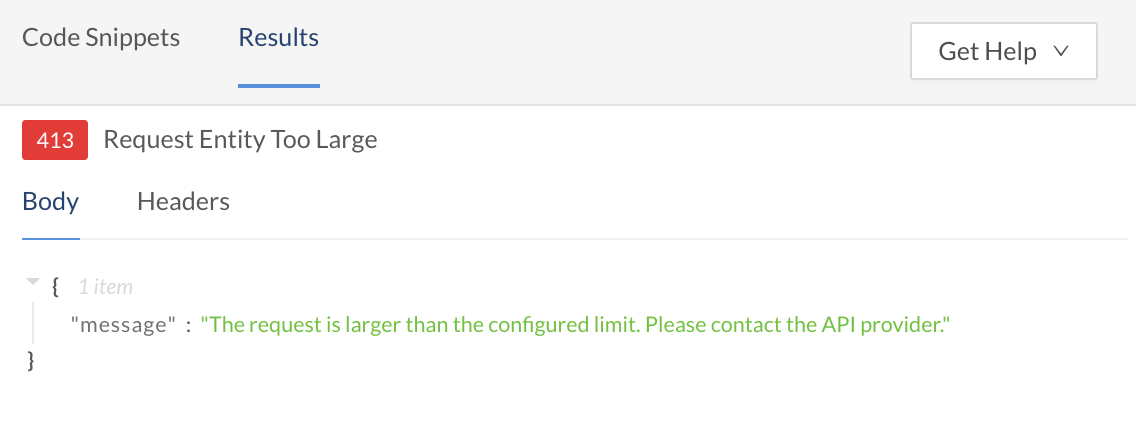
You can specify a maximum allowed request size (less than or equal to the default value 50 MB). If left empty or configured as 0, the default value is applied. The request size includes request line, header, and request body.

When the size of a request exceeds this limit, the request is blocked at the Rapid Runtime and a 413 status code is returned in the response.
Gateway timeout
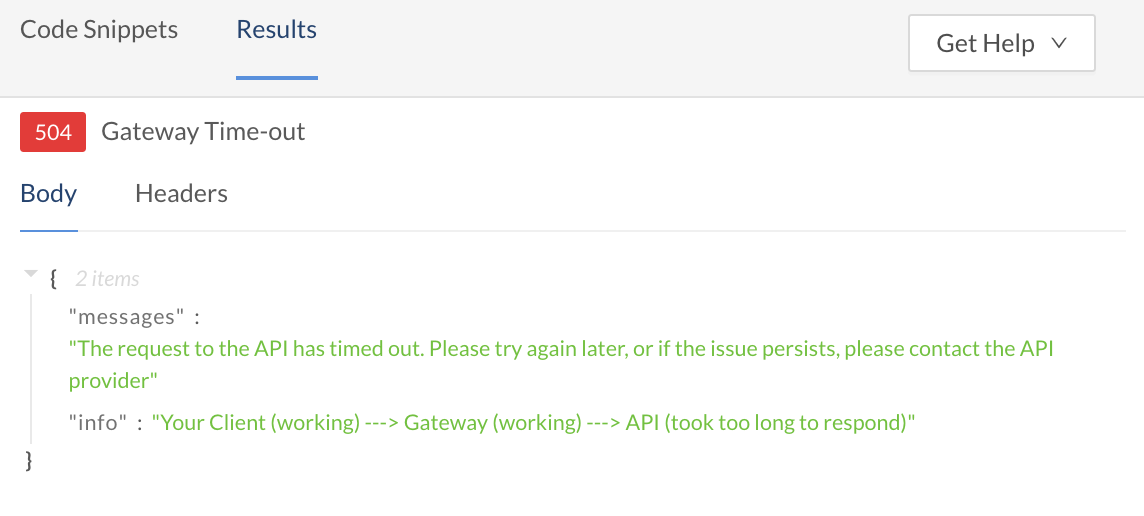
You can specify a maximum allowed time for the Rapid Runtime to wait for a response from the target API (less than or equal to the default value 180 seconds). If left empty or configured as 0, the default value is applied.

When the response from the target API takes longer than the specified timeout value, the Rapid Runtime terminates the call and a 504 status code is returned in the response.
Updated 7 months ago
